
You have a group of users that you want to only login into to certain devices in your organization. A good example is a general use account that you only use in one place (like a kiosk or a dedicated work area) but MFA is not feasible. You can use Conditional Access to help with this.
What is Conditional Access?
Conditional Access is a part of Azure AD that helps organizations improve security and compliance. By creating Conditional Access policies, you can tweak your authentication process.
Think about the old way of authentication: You require user to supply a username and password. Most of the time, it’s the legitimate account owner typing them in, the user can go on to access all the data, applications and other resources they’ve been granted permissions for. But consider this, an attacker has stolen or guessed a user’s credentials. Now they are accessing your network, and could have a breach on your hands
To mitigate these risks, organizations can put additional authentication in place. MFA is a good example.
The thing is, MFA is a broad approach. In the example I am about to show you what to do if the user is unable to use MFA.
You can use Azure AD Conditional to strengthen the authentication process. For example, you can create a policy to require users in a certain group to only login on devices that are recognized by the organization (At least Azure AD registered) and block all others. This will also help you pinpoint a breach a lot quicker. I will show you how in the next section.
Limit A Users Login With Conditional Access
Login to your Azure Active Directory (AD) portal and go to Conditional Access and add a new policy:

Give your Policy a name and then add users or groups that you want to include in this policy ( In my example I added a group):
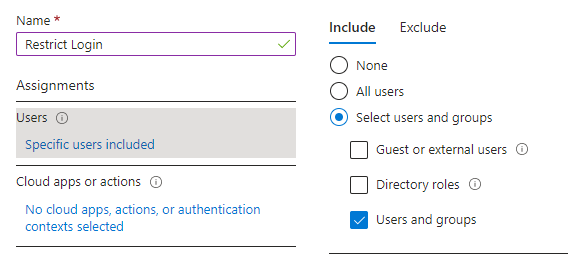
Next, you can move to the next step, which is what applications you want to restrict login to. In this example, I have chosen Office 365:

This is the most important part the Conditional Access Policy:
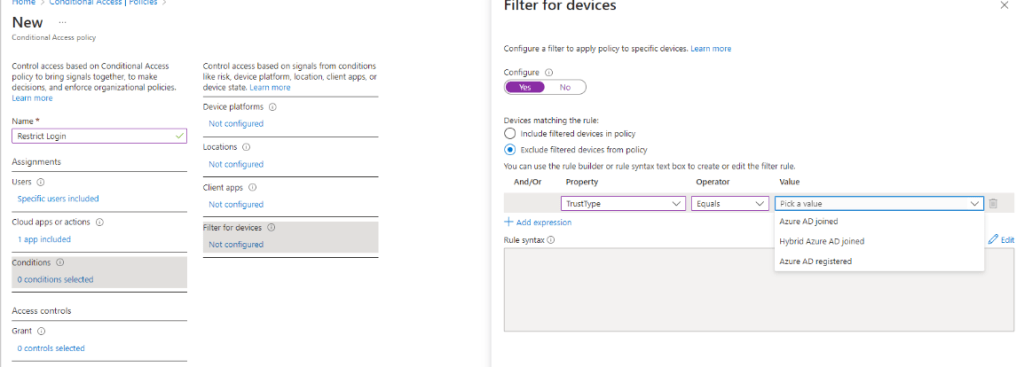
In the Filter for Devices Section, you exclude devices from the policy by “Trust type”. If a user account from the group specified above is NOT one or more of the trust types you specify, they ARE included. I kept it simple and chose Azure AD registered. I am in a Hybrid environment and our devices are not joined to the cloud, only registered.
The last section is to block all access to the aforementioned apps:

You could save the policy and start using it right away but that would not be a good idea. Save it as “Report-Only” and then check you Azure AD sign in logs to make sure it it working. Look at the logs by going to Azure AD / Users / Sign-in Logs. You will see a list of your users sign-ins. Filter for a time period where you have the Report-Only Conditional Access Policy in place.
Pick a user account that you know in included in the policy, if you see this then the policy would not block them if it were on:

If you see the following you the device would be blocked from signing in if it were on:

Users would expect to get this screen when they try to login:

You can investigate the sign-in to make sure it is not a false positive. Let the policy run in “Report-Only” Mode for awhile until you are sure it is running as it should and then turn it on. You have found a way to limit logging in for a certain group of users where MFA is not feasible.
Happy IT’ing
Dan
